Lessons I Learned From Tips About How To Detect Conficker On A Network
The latest nmap release can test windows machines for conficker infection.
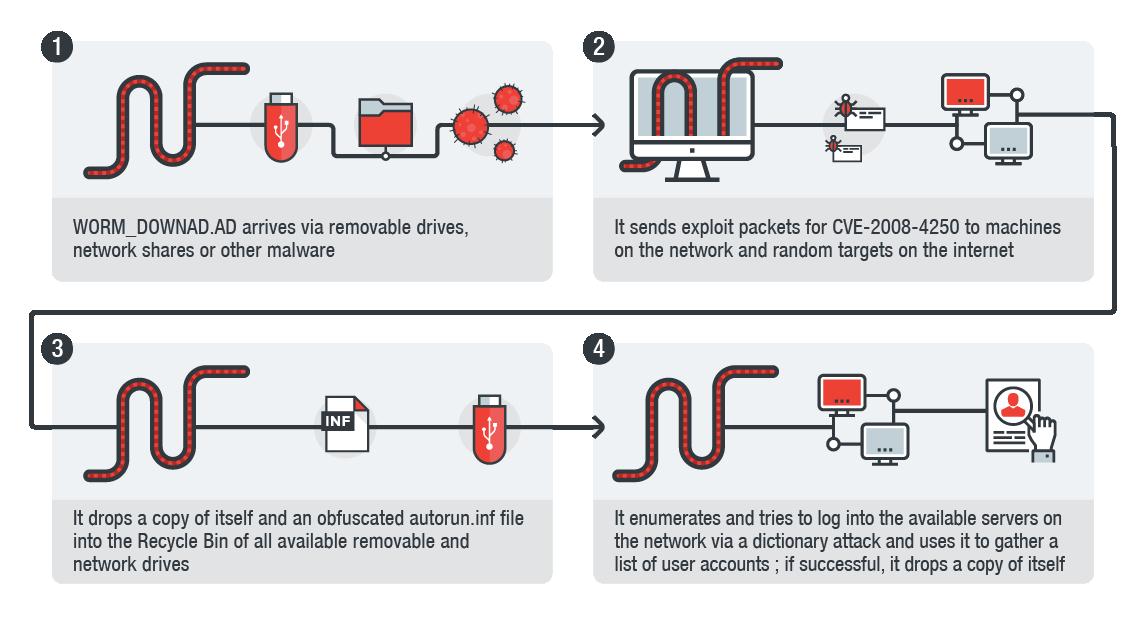
How to detect conficker on a network. For conficker, following levels of security are provided: I figure everyone is good and ready for tomorrow but just in case you want to double check or still need to scan your network here is a quick and easy method with nmap. There are three options in the above command to help cut down on the amount of work nmap has to do per host:
Open the new gpo, and then move to the following folder: You can download the latest nmap for os x. March 30, 2009 | 1 min read nessus plugin # 36036 performs a network based check for windows computers infected with a variant of the conficker virus.
It requires that “probe services on every port” be enabled. In the nessus scan policy. In addition, all the major security vendors are able to detect conficker and remove it.
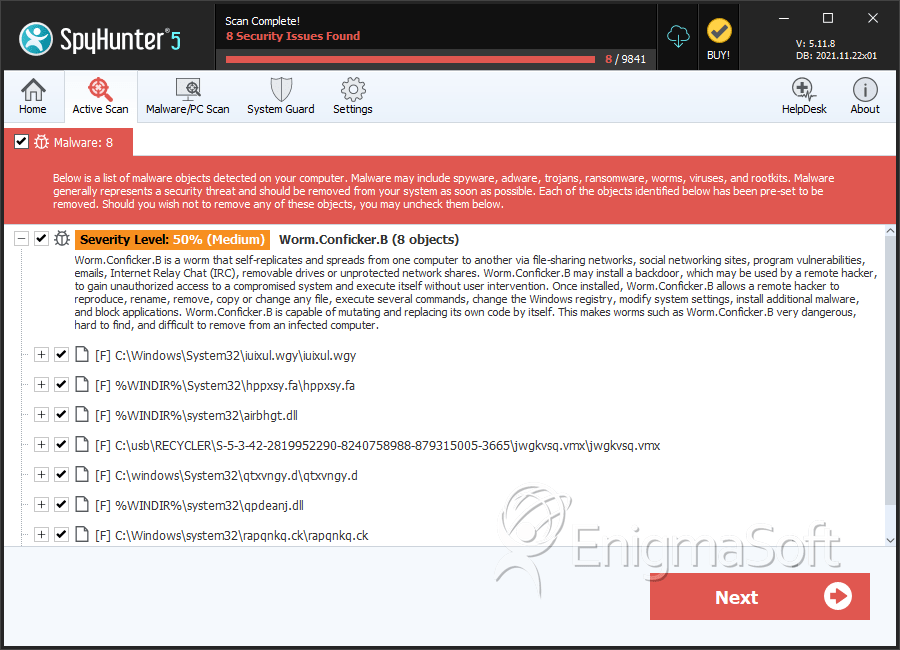
After being infected i tried using the enigma conficker remover tool, which first cleaned my system, the problem is that after i got connected to a computer on the network or. Typically this is a record of. If you are running linux, nmap may already be installed.
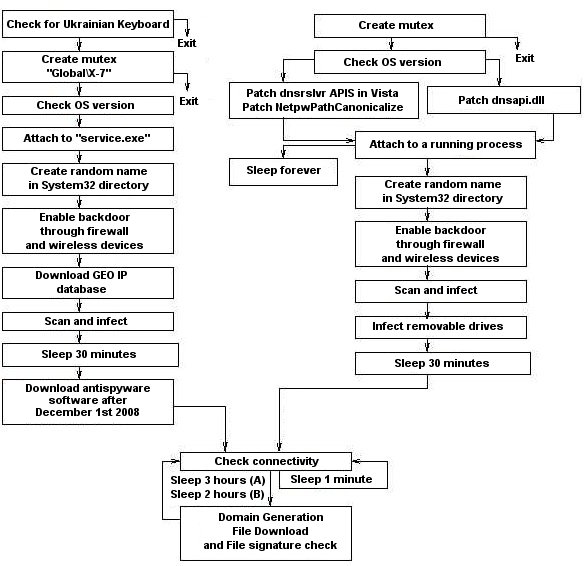
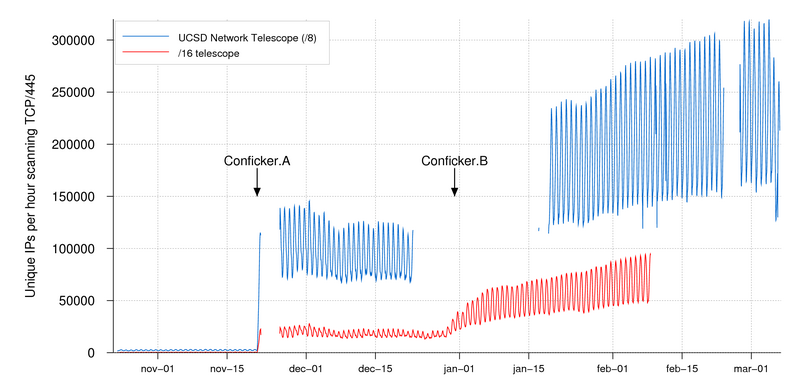
The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. Beyond the obvious, however, there are several things users can do.






/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)